How Portal to Bitcoin Blocks 3 Infamous Exploits
This article analyses three historical exploits that exemplify these failure modes and illustrates how Portal to Bitcoin’s architecture eliminates such risks.
Cross-chain communication protocols and AMM-based decentralised exchanges (DEXes) have driven significant innovation in DeFi, enabling the aggregation of liquidity and asset transfer across otherwise isolated blockchains.
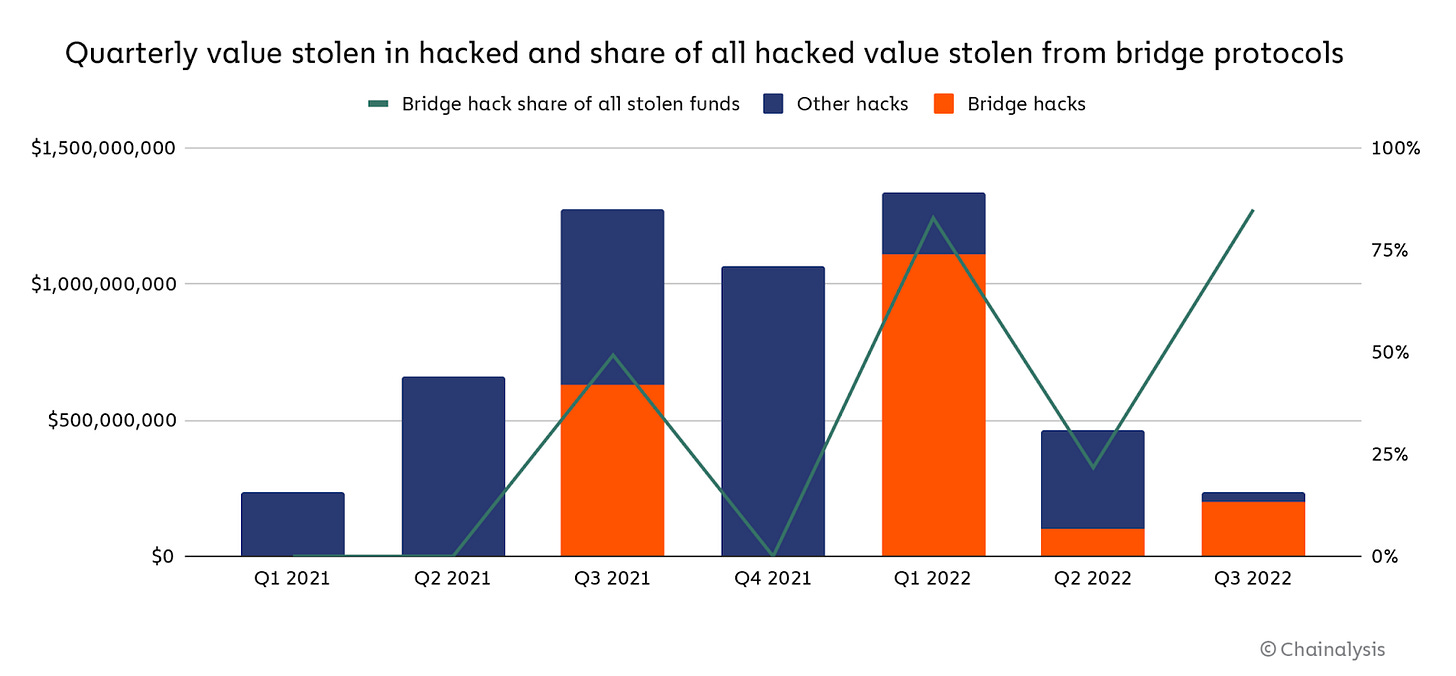
However, this progress has come at a steep cost: cross-chain infrastructure has become one of the largest attack surfaces in crypto. According to Chainalysis, over $2 billion was stolen from cross-chain bridges in 2022 alone.
The underlying causes of these failures stem from flawed trust assumptions, improper key management, insufficient input validation, and brittle messaging mechanisms.
This article analyses three historical exploits that exemplify these failure modes and illustrates how Portal to Bitcoin’s architecture eliminates such risks through hashed time-locked contracts (HTLCs), atomic swaps, and non-custodial coordination.
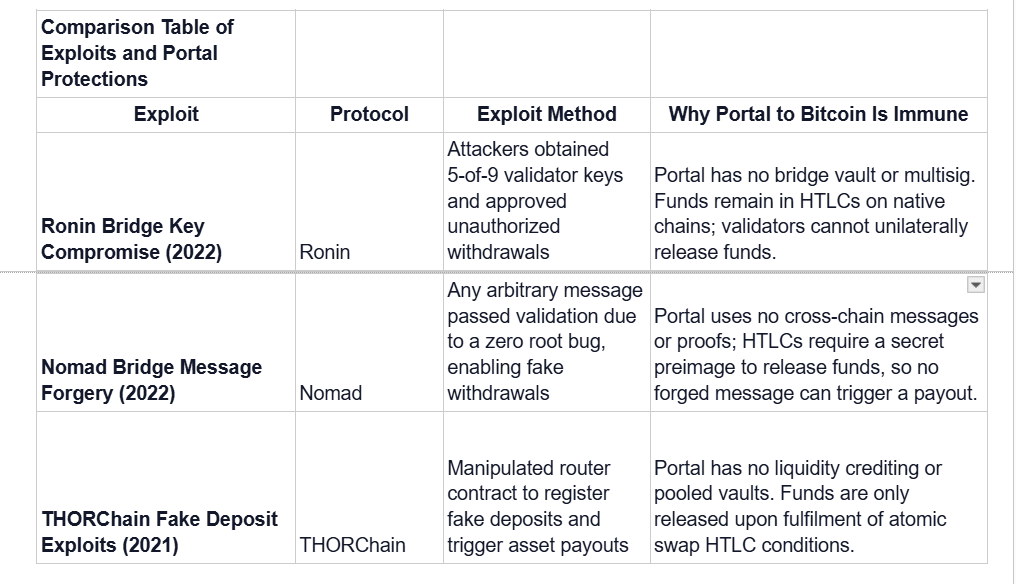
Exploit 1: Ronin Bridge Multi-Signature Compromise (2022)
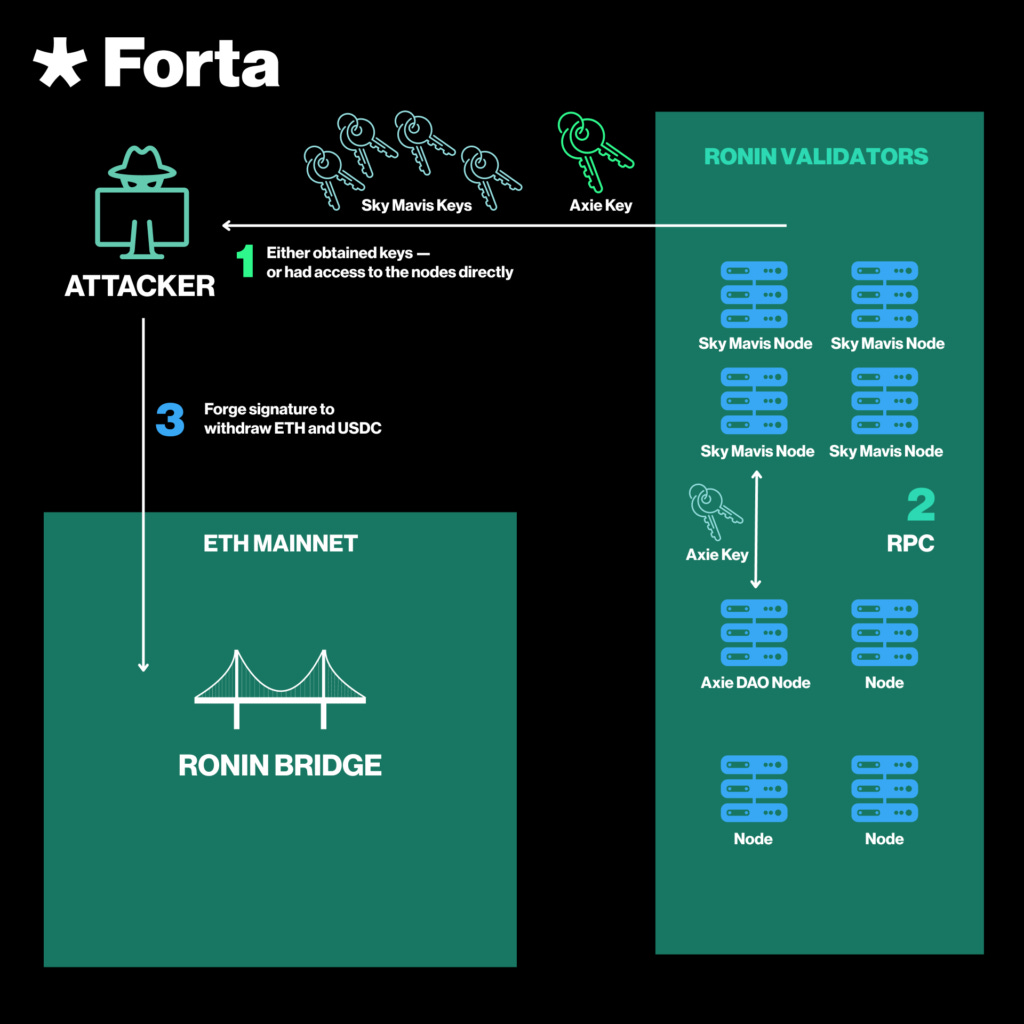
In March 2022, attackers compromised the Ronin Network bridge by gaining control of five out of nine validator keys. This allowed them to forge and approve unauthorised withdrawals. The forged transactions were submitted directly to the Ethereum mainnet, where the bridge’s smart contract verified only that they bore valid signatures from five validators.
It did not check for abnormal patterns or rates of withdrawal. The attackers created transactions that drained over $600 million from the bridge’s pooled funds in two massive transfers, moving ETH and USDC to their own wallets.
The breach went undetected for over a week, largely due to a lack of real-time monitoring on large bridge withdrawals and validator activity. The attack relied on spear-phishing and exploiting leftover privileged RPC access, enabling the attackers to sign as the Axie DAO validator alongside compromised Sky Mavis-controlled nodes.
Vulnerability in Protocol Design
The Ronin bridge operated a lock-and-mint model with a central bridge contract holding all user-deposited assets on Ethereum. Withdrawals were guarded by a 5-of-9 multisignature scheme, but the validator set was small and centralised, with Sky Mavis operating four validators itself.
A compromise of just one external validator key was enough to meet the threshold. There was no second layer of validation beyond multisig approval, and no on-chain logic that could independently detect forged transactions or require additional cryptographic proofs. Once quorum was achieved, any transaction could move funds from the bridge vault.
Why This Is Impossible on Portal to Bitcoin
Portal to Bitcoin does not aggregate assets into a central bridge contract. Instead, swaps are conducted via HTLCs where funds remain on their native chains. Validators coordinate the discovery of counterparties and monitor swap execution but have no custody over assets.
Even if all validators were compromised, they could not authorise unauthorised withdrawals because no validator signatures can trigger the release of funds. Funds are locked in contracts that require a specific hash preimage and timelock conditions to be met. The lack of a pooled vault or bridge wallet removes the incentive and ability for attackers to target multisignature key compromise as an attack vector.
Exploit 2: Nomad Bridge Message Forgery (2022)
Nomad Bridge suffered a critical failure in August 2022 when attackers exploited a misconfiguration in the Replica contract’s initialisation logic. The contract incorrectly treated the zero hash as a valid committed root, effectively causing all Merkle proofs to pass validation by default. Attackers submitted transactions calling the process() function on the Replica contract with arbitrary data.
The contract accepted these transactions without verifying legitimate proof, enabling attackers to transfer funds from the bridge’s pool on the destination chain to their addresses. This exploit turned into a free-for-all as dozens of copycats replicated the attack, draining over $190 million within hours. The entire validation mechanism of the bridge collapsed due to this single initialisation bug.
Vulnerability in Protocol Design
Nomad’s bridge relied on an optimistic message-passing mechanism. Messages originating on the home chain were supposed to be verified on the destination chain via Merkle proofs.
The bug in setting the initial committed root as the zero hash caused the Replica contract to treat any message as valid if it referred to that root. There was no fallback safeguard or multi-layer validation. With the contract holding pooled funds, the acceptance of arbitrary messages directly led to catastrophic fund loss.
Why This Is Impossible on Portal to Bitcoin
Portal to Bitcoin does not use cross-chain message passing, Merkle roots, or proofs to authorise fund movement. There are no bridge contracts processing messages from remote chains. Every swap consists of two HTLCs, one on each chain, where funds are only released upon valid revelation of a cryptographic secret matching a pre-agreed hash within the specified timelock.
A forged message or invalid proof has no place to act because no contract accepts such inputs. The atomic swap structure enforces that either both sides complete or both sides are refunded, with no central contract that can be tricked into releasing funds via fabricated messages.
Exploit 3: THORChain Fake Deposit Exploits (2021)
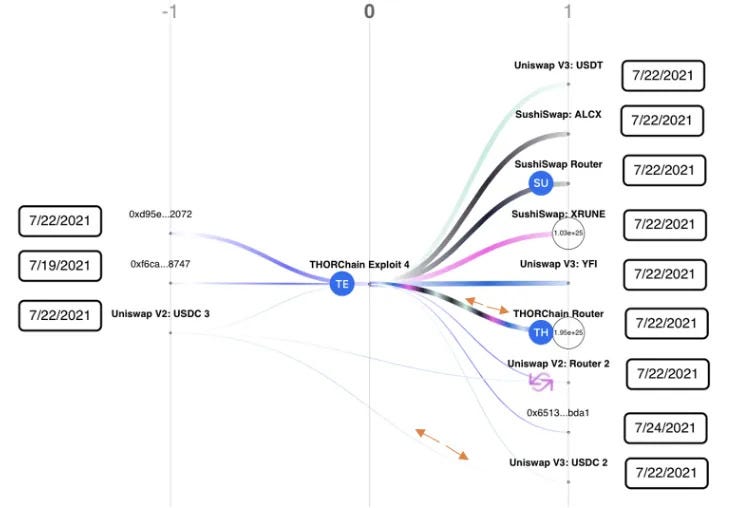
In July 2021, THORChain’s Ethereum Bifrost router was exploited twice. In the first exploit, an attacker submitted a 0 ETH deposit transaction but manipulated the router’s override logic to report a large deposit value to the system.
This caused THORChain to credit swap value to the attacker and release real assets from the pools. In the second exploit, an attacker crafted inputs to trigger a refund for a deposit that had never occurred, again draining pool funds. These exploits took advantage of weaknesses in deposit verification and accounting logic. Together, they cost THORChain millions in stolen funds.
Vulnerability in Protocol Design
THORChain’s design relies on vaults containing pooled assets controlled by validator consensus. Deposits are credited when validators observe them and consensus is reached. The Bifrost router logic trusted these deposit signals without fully validating actual receipt of value on-chain.
Attackers manipulated contract parameters and memo fields to create the illusion of deposits or failed transactions, tricking the system into disbursing real assets without real input.
Why This Is Impossible on Portal to Bitcoin
Portal to Bitcoin requires each swap participant to lock actual assets on-chain into an HTLC. No credit is issued based on deposit reports or signals. Funds can only be released when the counterpart HTLC on the other chain is properly funded and the secret preimage is revealed.
There are no pooled vaults or liquidity credits that can be exploited by fabricated inputs. Without pooled liquidity or accounting-based crediting, attackers have no avenue to trick the system into releasing funds for non-existent deposits.
Comparison Table
The table above summarises how three major cross-chain exploits targeted different architectural weaknesses, from key custody failures to message validation flaws and liquidity accounting errors. It highlights the fundamental difference in Portal to Bitcoin’s design, where HTLCs, native custody, and non-custodial coordination remove these attack vectors.
Final Thoughts
The exploits detailed in this report underscore how high-value cross-chain systems become prime targets when they rely on custodial bridges, weak validation logic, or flawed liquidity accounting. Ronin’s key compromise exposed the danger of over-centralised multisig setups, where control of a few keys can unlock vast reserves. Nomad’s message forgery highlighted how a single bug in cross-chain proof validation can collapse an entire bridge’s security.
THORChain’s fake deposit attacks showed that trusting reported deposits without hard on-chain verification opens the door to manipulation. Each case illustrates a different point of failure: key custody, message validation, and liquidity accounting, but they all share a common flaw: reliance on trust where it should not be required.
Portal to Bitcoin’s architecture eliminates these risks through structural choices. There are no bridge vaults for attackers to drain, no cross-chain messages or proofs that can be forged, and no pooled liquidity vulnerable to fake accounting. HTLCs ensure that funds are only released when strict cryptographic conditions are met, with native assets remaining on their original chains until swaps complete. Validators coordinate swaps but have no access to funds. This model provides deterministic security properties and sets a higher standard for cross-chain interoperability, proving that seamless trading does not require systemic vulnerability.